Page Summary
-
This audit identifies ad scripts injected into the page that may delay or prevent ad loading.
-
Use async script tags to improve loading speed, enabling the browser to fetch scripts earlier.
-
If the source of an injected ad script is unclear, Chrome DevTools' Network tab can be used to identify it.
-
A list of safe-to-load ad scripts is provided, including those from AdSense, Amazon, Criteo, Google Publisher Tag, and Index Exchange.
Overview
This audits checks whether or not ad scripts are being injected into the page. Other resources on the page may delay the fetching and loading of injected scripts, which will in turn delay the loading of ads. In some situations these scripts may not be fetched at all, preventing ads from being loaded all together.
Recommendations
Load scripts via async script tags to improve speed. The browser preload scanner can fetch script tags earlier, even if render blocking resources are blocking the script execution.
| Incorrect |
<script>
var el = document.createElement('script');
el.src = 'https://securepubads.g.doubleclick.net/tag/js/gpt.js';
var node = document.getElementsByTagName('script')[0];
node.parentNode.insertBefore(el, node);
</script> |
| Correct |
<script async src="https://securepubads.g.doubleclick.net/tag/js/gpt.js"></script> |
Identify the source of injected ad scripts
Sometimes it may not be obvious how an ad script is being injected into a page, or even that it's being injected at all. For example, when examining the source of a page after it's loaded, a script tag that has been injected may appear indistinguishable from a tag that was loaded statically.
In these cases, use the Network tab in Chrome DevTools to determine the source of injected ad scripts.
- Open DevTools by pressing
Control+Shift+JorCommand+Option+J(Mac). - Navigate to the Network tab.
- If not already visible, click Filter
 to open the filter bar and type the
name of the script flagged by this audit into the text box.
to open the filter bar and type the
name of the script flagged by this audit into the text box. - If not already visible, right-click on any table header and select Initiator to include the Initiator column in the network request waterfall table.
- Reload the page to capture network traffic.
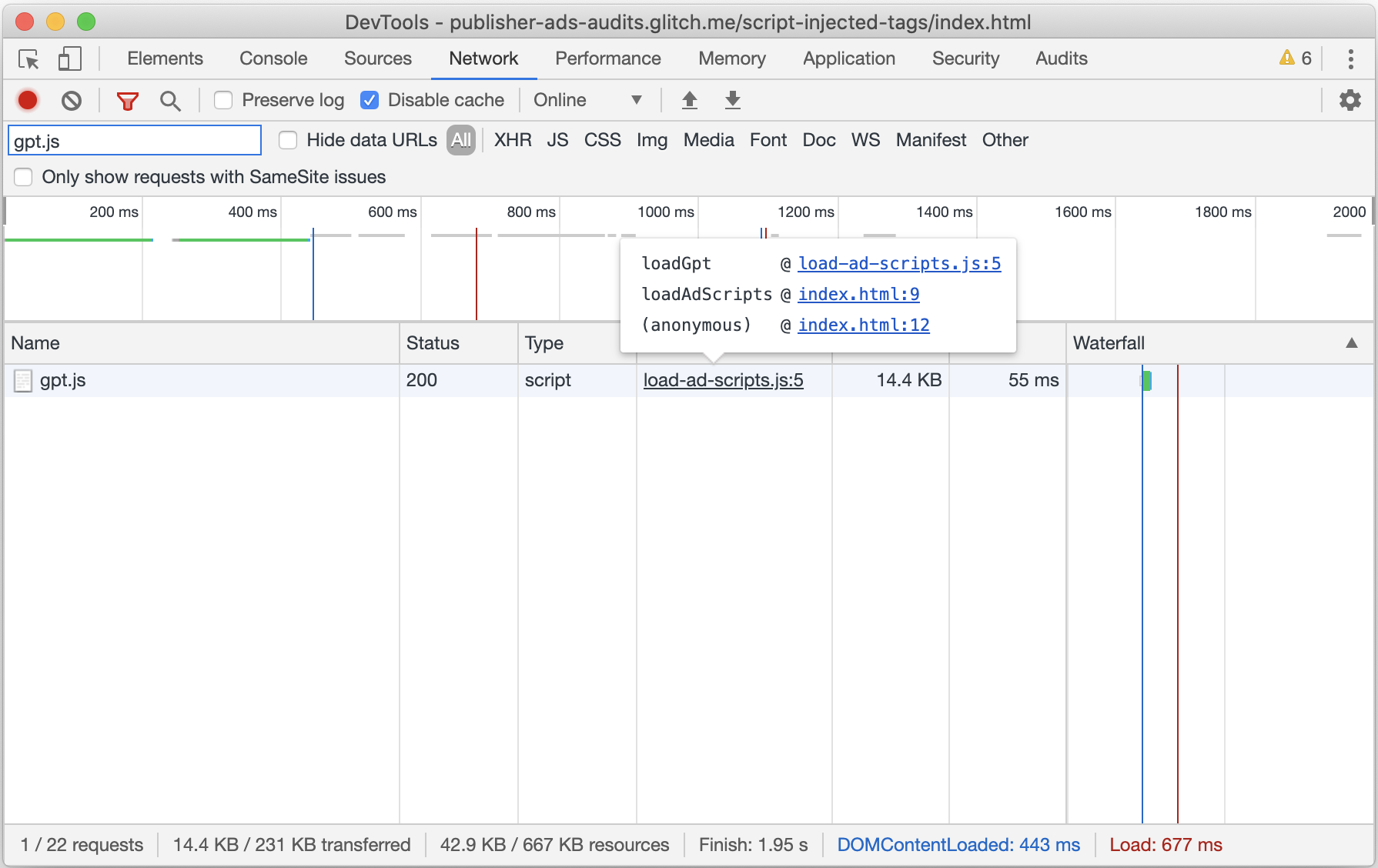
As seen in the above screenshot, the initiator column will contain information about the source of the script in question. You can click on the source link to jump directly to the code responsible for issuing the ad script request, or hover over the source link to see all of the calls leading up to the request.
More information
This audit operates against a allowlist of ad scripts which are known to be safe to load statically. The current list is:
| Library | Script(s) |
|---|---|
| AdSense |
pagead2.googlesyndication.com/pagead/js/adsbygoogle.js
|
| Amazon Publisher Services |
amazon-adsystem.com/aax2/apstag.js
|
| Criteo Direct Bidder |
static.criteo.net/js/*/publishertag.js
|
| Google Publisher Tag |
|
| Index Exchange |
js-sec.indexww.com/ht/p/*.js
|
Intervening against document.write()
Script-injected "async scripts" considered harmful
Speeding Up Async Snippets
