Page Summary
-
Google requires verification for Google OAuth clients requesting certain sensitive OAuth scopes, though Apps Script projects within the same Google Workspace domain or customer are exempt.
-
Unverified Apps Script projects using sensitive scopes and accessed by users outside the domain will display an "unverified app" screen and have a cap on the number of unverified users.
-
Verifying your app with Google removes the unverified app screen and the user cap, building user confidence.
-
To request verification, you need a website on a verified domain hosting publicly-accessible information about your app and privacy policy, along with a standard Google Cloud project you have edit access for.
-
The verification process involves completing the OAuth consent screen in your app's Google Cloud project with details like application name, logo, support email, scopes, authorized domains, and homepage and privacy policy URLs.
Google OAuth clients that request certain sensitive OAuth scopes are subject to verification by Google.
If you don't verify your script project's OAuth client, users outside your domain see an unverified app screen when they try to authorize your script. An unverified authorization flow allows these users to authorize unverified apps and use them, but only after confirming they understand the risks. The total number of unverified app users is also capped.
For more information, see the following articles:
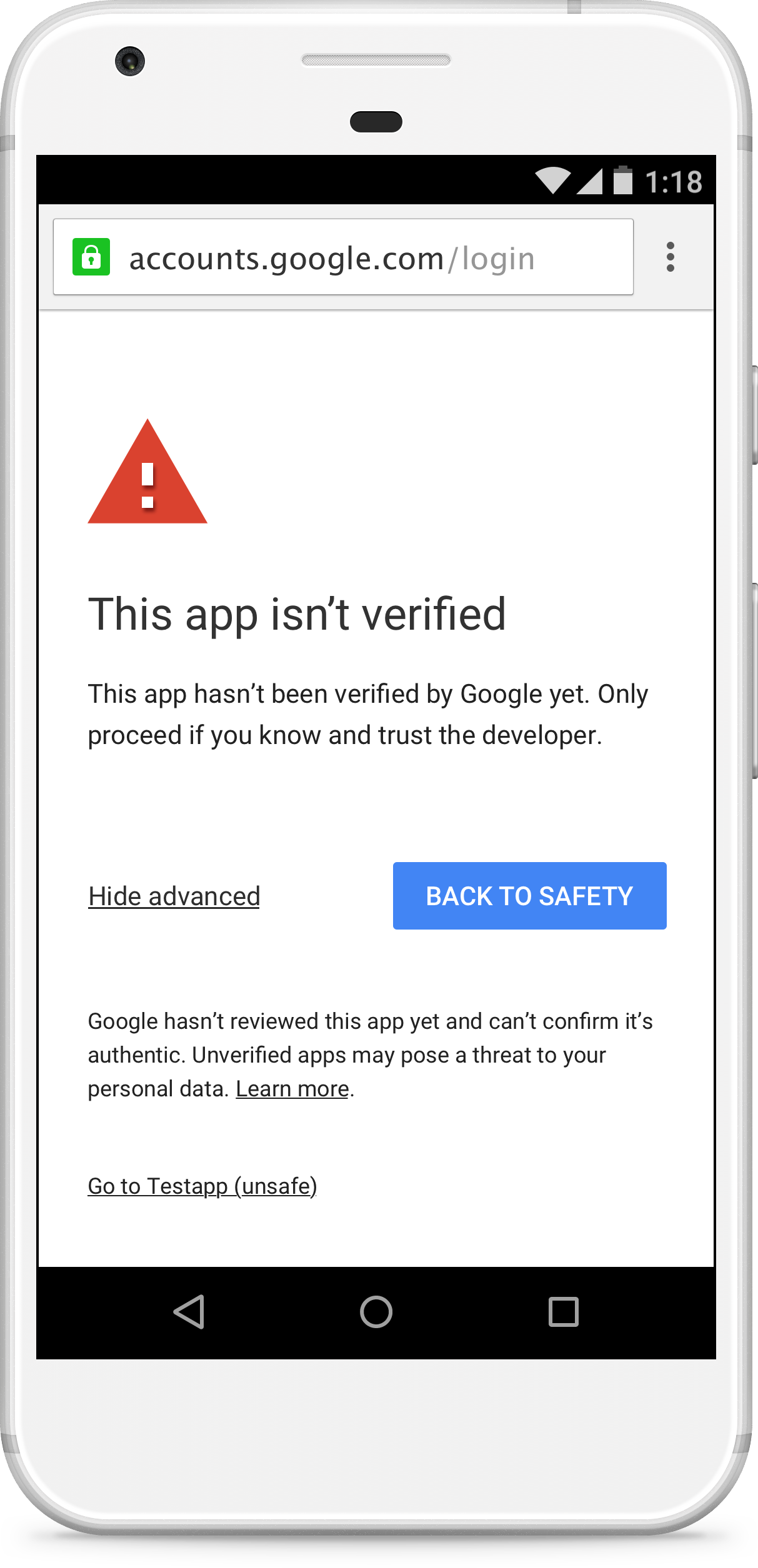
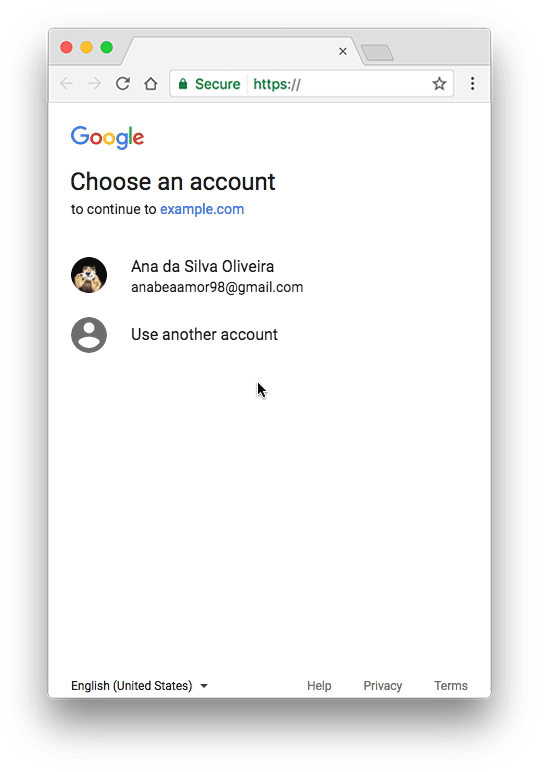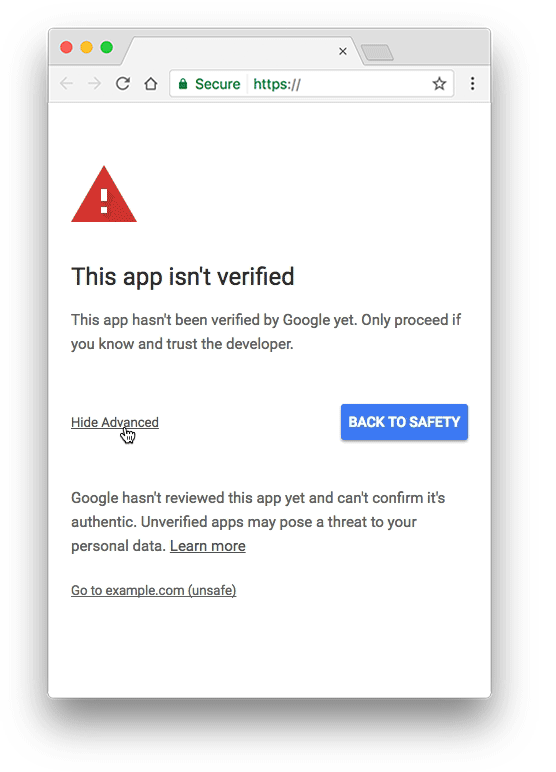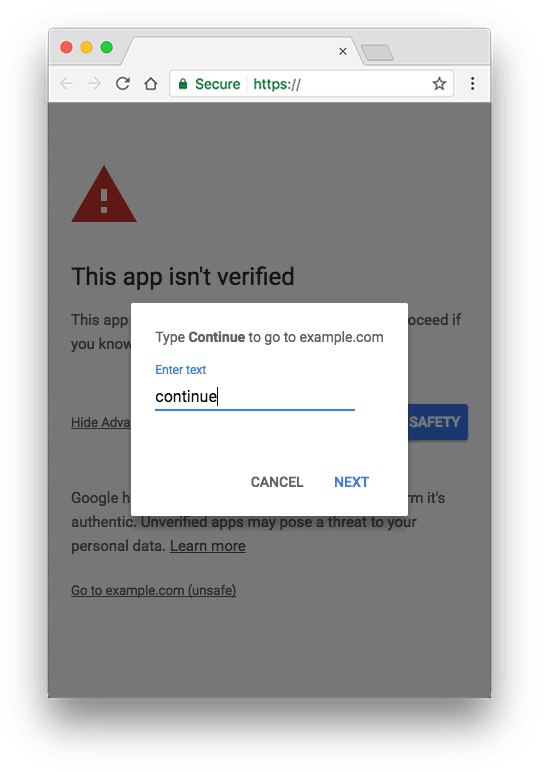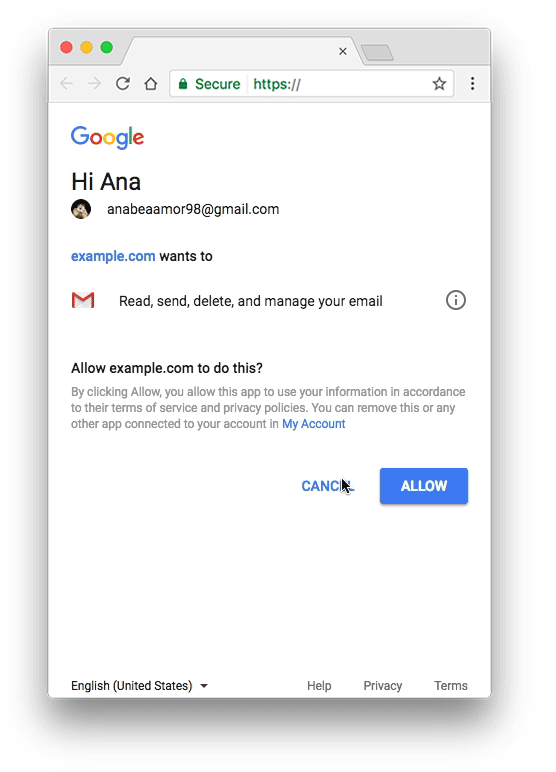
This change applies to Google OAuth web clients, including those used by all Apps Script projects. By verifying your app with Google, you can remove the unverified app screen from your authorization flow and give your users confidence that your app is non-malicious.
Unverified apps
Add-ons, web apps, and other deployments (such as apps that use the Apps Script API) may need verification.
Applicability
If the app uses sensitive OAuth scopes, the unverified app screen may appear as part of the authorization flow. Its presence (and the resulting unverified app authorization flow) depends on what account the app is published from and what account is attempting to use the app. For example, apps published internally within a specific Google Workspace organization don't result in the unverified app authorization flow for accounts in that domain, even if the app hasn't been verified.
The following table illustrates what situations result in the unverified app authorization flow:
| Client is verified | Publisher is a Google Workspace account of customer A | Script is in a shared drive of customer A | Publisher is a Gmail account | |
|---|---|---|---|---|
| User is a Google Workspace account of customer A | Normal auth flow | Normal auth flow | Normal auth flow | Unverified auth flow |
| User is a Google Workspace account not of customer A | Normal auth flow | Unverified auth flow | Unverified auth flow | Unverified auth flow |
| User is a Gmail account1 | Normal auth flow | Unverified auth flow | Unverified auth flow | Unverified auth flow |
1Any Gmail account, including the account used to publish the app.
User cap
The number of users who can authorize an app via the unverified app flow is capped to limit possible abuse. See OAuth application user limits for details.
Requesting verification
You can request a verification of the OAuth client used by your app and its associated Cloud Platform (GCP) project. Once your app is verified, your users will no longer see the unverified app screen. In addition, your app will no longer be subject to the user cap.
Requirements
In order to submit your OAuth client for verification, you must satisfy the following requirements:
You must own a web site on a domain. The site must host publicly-accessible pages that describe your app and its privacy policy. You must also verify your ownership of the site with Google.
The Google Cloud project your script project uses must be a standard Google Cloud project that you have edit access for. If your script is using its default Google Cloud project, you must switch to a standard Google Cloud project.
In addition, you must have the following required assets:
- Application name. The name of the app; this is displayed on the consent screen. It should match the name used for the app in other locations, such as the Google Workspace Marketplace listing for published apps.
- Application logo. A app logo JPEG, PNG, or BMP image to use in the consent screen. Its file size must be 1MB or less.
- Support email. This is an email displayed on the consent screen for users to contact if they need app support. It can be your email address or a Google Group that you own or manage.
- Scopes. The list of all the scopes your app uses. You can view your scopes in the Apps Script editor.
- Authorized domains. This is a list of domains containing information about your app. All your application's links (such as its required privacy policy page) must be hosted on authorized domains.
- Application homepage URL. The location of a homepage describing your app. This location must hosted on an authorized domain.
- Application privacy policy URL. The location of a page describing your app's privacy policy. This location must be hosted on an authorized domain.
In addition to the above required assets, you can optionally provide an Application terms of service URL that points to a page describing your app's terms of service. If provided, this location must be in an authorized domain.
Steps
- If you have not done so already, verify ownership of all the authorized domains you use to host your script project's privacy policy and other information. The verified owners of the domains must be editors or the owner of the script project.
- In the Apps Script project, click Overview . Under Project OAuth Scopes, copy the scopes that your script project uses.
Complete the OAuth consent screen for your application's Google Cloud project using the text and URL assets you collected.
- List the Authorized domains where your app's information (such as its privacy policy) are hosted.
To add your application scopes, click Add or Remove Scopes. The resulting dialog attempts to autodetect scopes for APIs you've enabled in the Google Cloud console (such as advanced services). You can select scopes from this list by checking the corresponding boxes.
This autodetected list doesn't always include scopes used by Apps Script built-in services. You must enter these scopes under Manually add scopes.
When you're done, click Update.
When you've entered all the required information, click Save.
Click Submit for verification to start a verification request.
Most verification requests receive a response within 24 to 72 hours. You can check the Verification status at the top of the OAuth consent screen form. When verification of your OAuth client is confirmed, your app is verified.