Digital IDs can be accepted both in-app and web flows. To accept credentials from Google Wallet you will need to:
- Integrate using app or web following the provided instructions.
- Use the test ID to test your flow using Google Wallet sandbox.
- To go live, fill out this form to request access and accept the Google Wallet credential terms of service. You are required to fill it out for each of your business entities. Our team will get in touch with you after you fill out the form.
- If you have questions, you can reach out to
wallet-identity-rp-support@google.com.
Supported Credential Formats
Several proposed standards exist that define the data format of digital identity documents, with two gaining significant industry traction:
- mdocs - defined by ISO.
- w3c Verifiable Credentials - defined by the w3c.
While the Android Credential Manager supports both formats, Google Wallet supports only mdoc based Digital IDs at the moment.
Supported Credentials
Google Wallet supports 2 credential types:
- Mobile Driver's License (mDL)
- ID pass
You can request either credential in your flow with a single parameter change.
User experience
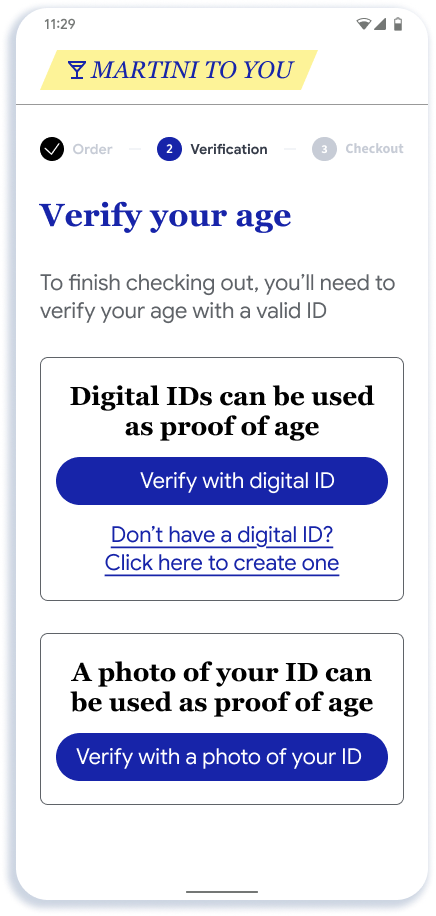
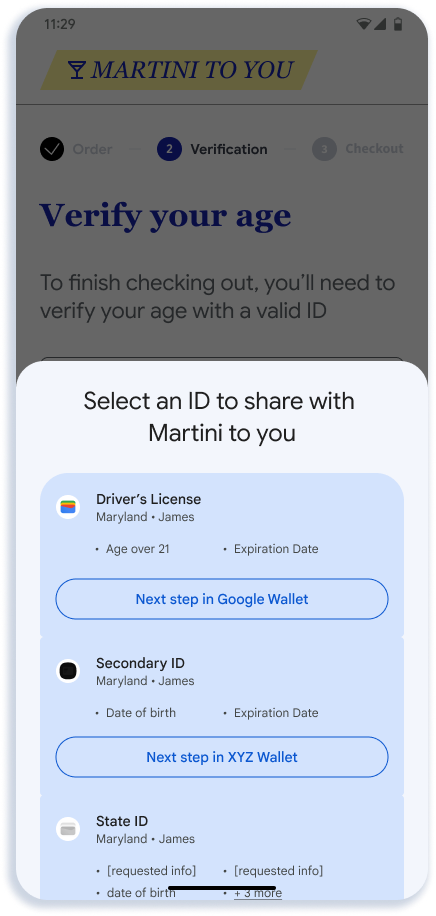
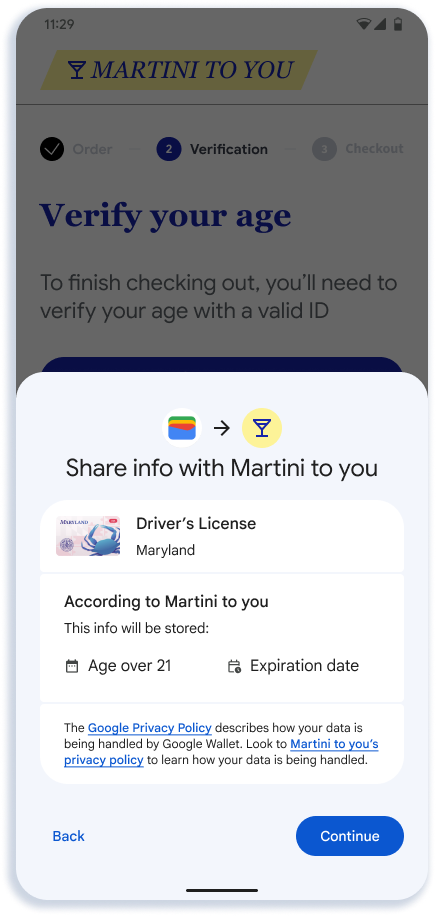
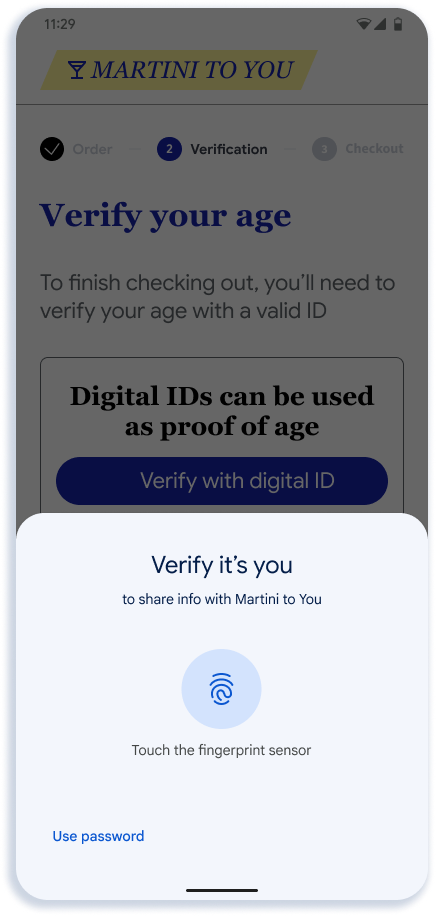
This section describes the recommended online presentation flow. The flow shows the presentation of age to an app for alcohol delivery, but the UX is similar for web and other types of presentations.
 |
 |
 |
 |
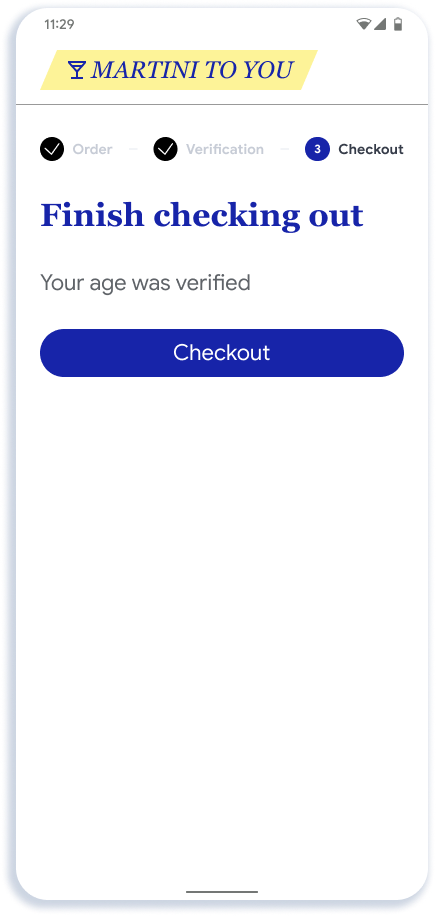 |
| User prompted to verify age in app or website | User sees available eligible credentials | User sees confirmation page in Google Wallet | User Authenticates to confirm sharing | Data sent to app or website |
Key Notes
- The app or website has flexibility in how it creates the entry point to the API. As shown in Step 1, we recommend showing a generic button such as "Verify with digital ID" since over time we expect options beyond Google Wallet to be available through the API.
- The selector screen in Step 2 is rendered by Android. Eligible credentials are determined by a match between the registration logic provided by each Wallet and the request sent by the relying party.
- Step 3 is rendered by Google Wallet. Google Wallet will show the name, logo, and privacy policy that the developer provides on this screen.
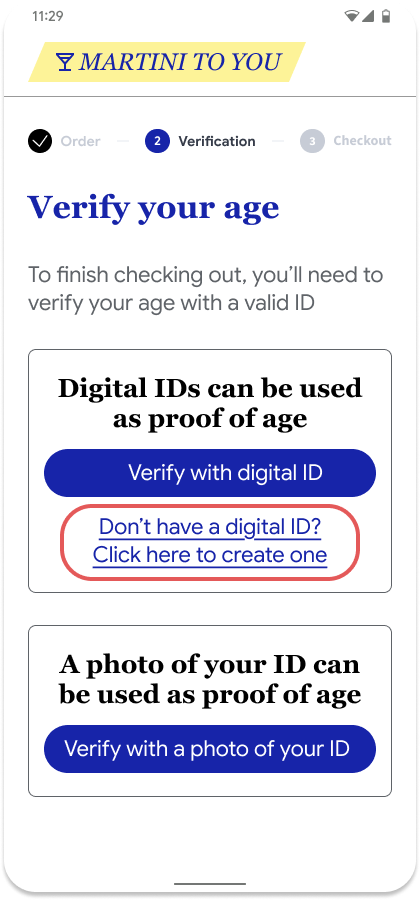
Add a digital ID flow
If the user does not have a credential, we recommend providing a link next to the "Verify with digital ID" button, which will deep-link to Google Wallet so the user can add a digital ID.
 |
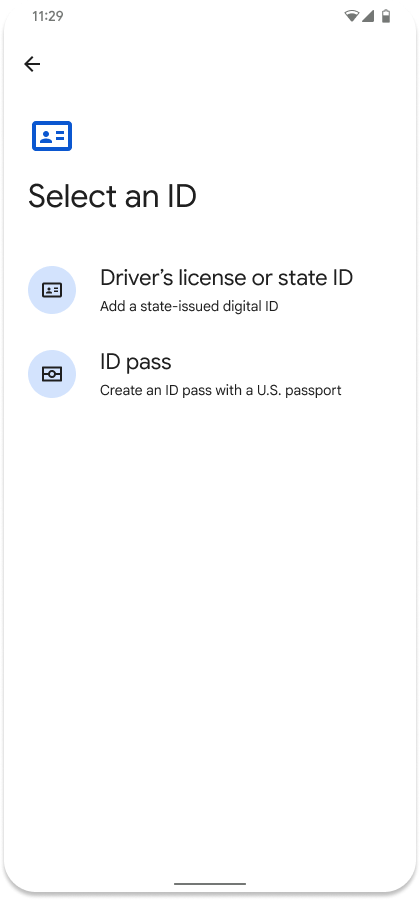 |
| User prompted to verify age in app or website | User taken to Google Wallet to get a digital ID |
No digital ID available
If the user selects the "Verify with digital ID" option without having a digital ID, they will be shown this error message.
 |
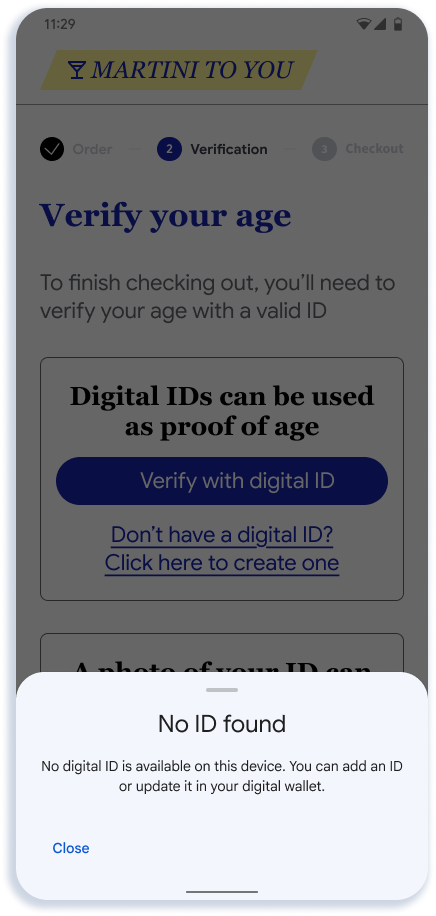 |
| User prompted to verify age in app or website | User shown an error if they don't have a digital ID |
The API does not support a feature to silently learn whether the user has any available digital IDs to preserve the user's privacy. Hence, we recommend including the onboarding link option, as shown.
Request Format for requesting ID credentials from wallet
Here is a sample of an mdoc requestJson request to get identity credentials
from any wallet on an Android device or web.
{
"requests" : [
{
"protocol": "openid4vp-v1-unsigned", // openid4vp-v1-signed for signed request.
"data": {<credential_request>} // This is an object, shouldn't be a string.
}
]
}
Request Encryption
The client_metadata contains the encryption public key for each request.
You'll need to store private keys for each request and use them to authenticate
and authorize the token that you receive from the wallet app.
The credential_request parameter in requestJson contains the following
fields.
Specific Credential
{
"response_type": "vp_token",
"response_mode": "dc_api.jwt", // change this to dc_api if you want to demo with a non encrypted response.
"nonce": "1234",
"dcql_query": {
"credentials": [
{
"id": "cred1",
"format": "mso_mdoc",
"meta": {
"doctype_value": "org.iso.18013.5.1.mDL" // this is for mDL. Use com.google.wallet.idcard.1 for ID pass
},
"claims": [
{
"path": [
"org.iso.18013.5.1",
"family_name"
],
"intent_to_retain": false // set this to true if you are saving the value of the field
},
{
"path": [
"org.iso.18013.5.1",
"given_name"
],
"intent_to_retain": false
},
{
"path": [
"org.iso.18013.5.1",
"age_over_18"
],
"intent_to_retain": false
}
]
}
]
},
"client_metadata": {
"jwks": {
"keys": [ // sample request encryption key
{
"kty": "EC",
"crv": "P-256",
"x": "pDe667JupOe9pXc8xQyf_H03jsQu24r5qXI25x_n1Zs",
"y": "w-g0OrRBN7WFLX3zsngfCWD3zfor5-NLHxJPmzsSvqQ",
"use": "enc",
"kid" : "1", // This is required
"alg" : "ECDH-ES", // This is required
}
]
},
"vp_formats_supported": {
"mso_mdoc": {
"deviceauth_alg_values": [
-7
],
"isserauth_alg_values": [
-7
]
}
}
}
}
Any Eligible Credential
Here is the example request for both mDL and ID pass. The user can proceed with either one.
{
"response_type": "vp_token",
"response_mode": "dc_api.jwt", // change this to dc_api if you want to demo with a non encrypted response.
"nonce": "1234",
"dcql_query": {
"credentials": [
{
"id": "mdl-request",
"format": "mso_mdoc",
"meta": {
"doctype_value": "org.iso.18013.5.1.mDL"
},
"claims": [
{
"path": [
"org.iso.18013.5.1",
"family_name"
],
"intent_to_retain": false // set this to true if you are saving the value of the field
},
{
"path": [
"org.iso.18013.5.1",
"given_name"
],
"intent_to_retain": false
},
{
"path": [
"org.iso.18013.5.1",
"age_over_18"
],
"intent_to_retain": false
}
]
},
{ // Credential type 2
"id": "id_pass-request",
"format": "mso_mdoc",
"meta": {
"doctype_value": "com.google.wallet.idcard.1"
},
"claims": [
{
"path": [
"org.iso.18013.5.1",
"family_name"
],
"intent_to_retain": false // set this to true if you are saving the value of the field
},
{
"path": [
"org.iso.18013.5.1",
"given_name"
],
"intent_to_retain": false
},
{
"path": [
"org.iso.18013.5.1",
"age_over_18"
],
"intent_to_retain": false
}
]
}
]
credential_sets : [
{
"options": [
[ "mdl-request" ],
[ "id_pass-request" ]
]
}
]
},
"client_metadata": {
"jwks": {
"keys": [ // sample request encryption key
{
"kty": "EC",
"crv": "P-256",
"x": "pDe667JupOe9pXc8xQyf_H03jsQu24r5qXI25x_n1Zs",
"y": "w-g0OrRBN7WFLX3zsngfCWD3zfor5-NLHxJPmzsSvqQ",
"use": "enc",
"kid" : "1", // This is required
"alg" : "ECDH-ES", // This is required
}
]
},
"vp_formats_supported": {
"mso_mdoc": {
"deviceauth_alg_values": [
-7
],
"isserauth_alg_values": [
-7
]
}
}
}
}
You can request any number of supported attributes from any identity credential stored in Google Wallet.
Signed Requests
To enhance security and ensure the integrity of your authentication requests, you should implement Signed Requests (also known as JWT Secured Authorization Requests or JAR). Refer to the openID4VP documentation for additional details.
Unlike unsigned requests where parameters are sent as raw JSON, a signed request encapsulates your Verifiable Presentation request inside a cryptographically signed JSON Web Token (JWT). This provides two main benefits:
- Integrity: Ensures the request has not been tampered with.
- Alternative Authentication Mechanisms (x509 PKI): Proves to Google Wallet that the request originated from a Verifier owning the specific public key registered with Google Wallet.
Prerequisites
Before implementing the code changes for signed request, ensure you have:
- Private Key: You need a private key (e.g., Elliptic Curve
ES256or RSA) to sign the request which is managed in your server. - Certificate: You need a standard X.509 certificate derived from your key pair.
- Registration: Ensure your public certificate is registered with Google Wallet. Reach out to our support team at
wallet-identity-rp-support@google.com
Update Request Construction Logic
The core change involves using your private key and wrapping the payload in a JWS.
def construct_openid4vp_request(
doctypes: list[str],
requested_fields: list[dict],
nonce_base64: str,
jwe_encryption_public_jwk: jwk.JWK,
is_zkp_request: bool,
is_signed_request: bool,
state: dict,
origin: str
) -> dict:
# ... [Existing logic to build 'presentation_definition' and basic 'request_payload'] ...
# ------------------------------------------------------------------
# SIGNED REQUEST IMPLEMENTATION (JAR)
# ------------------------------------------------------------------
if is_signed_request:
try:
# 1. Load the Verifier's Certificate
# We must load the PEM string into a cryptography x509 object
verifier_cert_obj = x509.load_pem_x509_certificate(
CERTIFICATE.encode('utf-8'),
backend=default_backend()
)
# 2. Calculate Client ID (x509_hash)
# We calculate the SHA-256 hash of the DER-encoded certificate.
cert_der = verifier_cert_obj.public_bytes(serialization.Encoding.DER)
verifier_fingerprint_bytes = hashlib.sha256(cert_der).digest()
# Create a URL-safe Base64 hash (removing padding '=')
verifier_fingerprint_b64 = base64.urlsafe_b64encode(verifier_fingerprint_bytes).decode('utf-8').rstrip("=")
# Format the client_id as required by the spec
client_id = f'x509_hash:{verifier_fingerprint_b64}'
# 3. Update Request Payload with JAR specific fields
request_payload["client_id"] = client_id
# Explicitly set expected origins to prevent relay attacks
if origin:
request_payload["expected_origins"] = [origin]
# 4. Create Signed JWT (JWS)
# Load the signing private key
signing_key = jwk.JWK.from_pem(PRIVATE_KEY.encode('utf-8'))
# Initialize JWS with the JSON payload
jws_token = jws.JWS(json.dumps(request_payload).encode('utf-8'))
# Construct the JOSE Header
# 'x5c' (X.509 Certificate Chain) is critical: it allows the wallet
# to validate your key against the one registered in the console.
x5c_value = base64.b64encode(cert_der).decode('utf-8')
protected_header = {
"alg": "ES256", # Algorithm (e.g., ES256 or RS256)
"typ": "oauth-authz-req+jwt", # Standard type for JAR
"kid": "1", # Key ID
"x5c": [x5c_value] # Embed the certificate
}
# Sign the token
jws_token.add_signature(
key=signing_key,
alg=None,
protected=json_encode(protected_header)
)
# 5. Return the Request Object
# Instead of returning the raw JSON, we return the signed JWT string
# under the 'request' key.
return {"request": jws_token.serialize(compact=True)}
except Exception as e:
print(f"Error signing OpenID4VP request: {e}")
return None
# ... [Fallback for unsigned requests] ...
return request_payload
In App
To request identity credentials from your Android apps, follow these steps:
Update dependencies
In your project's build.gradle, update your dependencies to use the Credential Manager (beta):
dependencies {
implementation("androidx.credentials:credentials:1.5.0-beta01")
implementation("androidx.credentials:credentials-play-services-auth:1.5.0-beta01")
}
Configure the Credential Manager
To configure and initialize a CredentialManager object, add logic similar
to the following:
// Use your app or activity context to instantiate a client instance of CredentialManager.
val credentialManager = CredentialManager.create(context)
Request Identity attributes
Instead of specifying individual parameters for identity requests, the app provides them all together as a JSON string within the CredentialOption. The Credential Manager passes this JSON string along to the available digital wallets without examining its contents. Each wallet is then responsible for: - Parsing the JSON string to understand the identity request. - Determining which of its stored credentials, if any, satisfy the request.
We recommend partners to create their requests on the server even for Android app integrations.
You'll use the requestJson from Request Format
as the request in the GetDigitalCredentialOption() function call.
// The request in the JSON format to conform with
// the JSON-ified Digital Credentials API request definition.
val requestJson = generateRequestFromServer()
val digitalCredentialOption =
GetDigitalCredentialOption(requestJson = requestJson)
// Use the option from the previous step to build the `GetCredentialRequest`.
val getCredRequest = GetCredentialRequest(
listOf(digitalCredentialOption)
)
coroutineScope.launch {
try {
val result = credentialManager.getCredential(
context = activityContext,
request = getCredRequest
)
verifyResult(result)
} catch (e : GetCredentialException) {
handleFailure(e)
}
}
Verify and Validate the response
Once you get a response back from the wallet, you will verify whether the
response is successful and contains the credentialJson response.
// Handle the successfully returned credential.
fun verifyResult(result: GetCredentialResponse) {
val credential = result.credential
when (credential) {
is DigitalCredential -> {
val responseJson = credential.credentialJson
validateResponseOnServer(responseJson) // make a server call to validate the response
}
else -> {
// Catch any unrecognized credential type here.
Log.e(TAG, "Unexpected type of credential ${credential.type}")
}
}
}
// Handle failure.
fun handleFailure(e: GetCredentialException) {
when (e) {
is GetCredentialCancellationException -> {
// The user intentionally canceled the operation and chose not
// to share the credential.
}
is GetCredentialInterruptedException -> {
// Retry-able error. Consider retrying the call.
}
is NoCredentialException -> {
// No credential was available.
}
else -> Log.w(TAG, "Unexpected exception type ${e::class.java}")
}
}
The credentialJson response contain an encrypted identityToken (JWT),
defined by the W3C. The Wallet app is responsible for crafting this response.
Example:
{
"protocol" : "openid4vp-v1-unsigned",
"data" : {
<encrpted_response>
}
}
You'll pass this response back to the server to validate it's authenticity. You can find the steps to validate credential response.
Web
To request Identity Credentials using the Digital Credentials API on Chrome or other supported browsers, make the following request.
const credentialResponse = await navigator.credentials.get({
digital : {
requests : [
{
protocol: "openid4vp-v1-unsigned",
data: {<credential_request>} // This is an object, shouldn't be a string.
}
]
}
})
Send the response from this api back to your server to validate credential response
Steps to Validate credential response
Upon receiving the encrypted identityToken from your app or website, there are multiple validations you'll need to perform before trusting the response.
Decrypt response using the private key
The first step is to decrypt the token using the saved private key and obtain a response JSON.
Python Example:
from jwcrypto import jwe, jwk # Retrieve the Private Key from Datastore reader_private_jwk = jwk.JWK.from_json(jwe_private_key_json_str) # Save public key thumbprint for session transcript encryption_public_jwk_thumbprint = reader_private_jwk.thumbprint() # Decrypt the JWE encrypted response from Google Wallet jwe_object = jwe.JWE() jwe_object.deserialize(encrypted_jwe_response_from_wallet) jwe_object.decrypt(reader_private_jwk) decrypted_payload_bytes = jwe_object.payload decrypted_data = json.loads(decrypted_payload_bytes)decrypted_datawill result in avp_tokenJSON containing the credential{ "vp_token": { "cred1": ["<base64UrlNoPadding_encoded_credential>"] // This applies to OpenID4VP 1.0 spec. } }Create the session transcript
The next step is to create the SessionTranscript from ISO/IEC 18013-5:2021 with an Android or Web specific Handover structure:
SessionTranscript = [ null, // DeviceEngagementBytes not available null, // EReaderKeyBytes not available [ "OpenID4VPDCAPIHandover", AndroidHandoverDataBytes // BrowserHandoverDataBytes for Web ] ]For both Android and web handovers, you'll need to use the same nonce that you used to generate
credential_request.Android Handover
AndroidHandoverData = [ origin, // "android:apk-key-hash:<base64SHA256_ofAppSigningCert>", nonce, // nonce that was used to generate credential request, encryption_public_jwk_thumbprint, // Encryption public key (JWK) Thumbprint ] AndroidHandoverDataBytes = hashlib.sha256(cbor2.dumps(AndroidHandoverData)).digest()
Browser Handover
BrowserHandoverData =[ origin, // Origin URL nonce, // nonce that was used to generate credential request encryption_public_jwk_thumbprint, // Encryption public key (JWK) Thumbprint ] BrowserHandoverDataBytes = hashlib.sha256(cbor2.dumps(BrowserHandoverData)).digest()
Using the
SessionTranscript, the DeviceResponse must be validated according to ISO/IEC 18013-5:2021 clause 9. This includes several steps, such as:Check the State Issuer Cert. Refer to the supported issuer's IACA certs.
Verify MSO signature (18013-5 Section 9.1.2)
Calculate and check ValueDigests for Data Elements (18013-5 Section 9.1.2)
Verify
deviceSignaturesignature (18013-5 Section 9.1.3)
{
"version": "1.0",
"documents": [
{
"docType": "org.iso.18013.5.1.mDL",
"issuerSigned": {
"nameSpaces": {...}, // contains data elements
"issuerAuth": [...] // COSE_Sign1 w/ issuer PK, mso + sig
},
"deviceSigned": {
"nameSpaces": 24(<< {} >>), // empty
"deviceAuth": {
"deviceSignature": [...] // COSE_Sign1 w/ device signature
}
}
}
],
"status": 0
}
Build your solution
To build your solution, you can refer to the Identity Verifiers Reference Implementation on GitHub
Zero Knowledge Proof (ZKP) based verification
Zero-Knowledge Proof (ZKP) is a cryptographic method that allows an individual (the prover) to prove to a verifier that they possess a certain piece of identity information or meet a specific criterion (e.g., are over 18, hold a valid credential) without revealing the actual underlying data itself. Essentially, it's a way to confirm the truth of a statement about one's identity while keeping the sensitive details private.
Digital identity systems that rely on direct sharing of identity data often require users to share excessive personal information, increasing the risk of data breaches and identity theft. ZKPs offer a paradigm shift, enabling verification with minimal disclosure.
Key Concepts of ZKPs in Digital Identity:
- Prover: The individual trying to prove an aspect of their identity.
- Verifier: The entity requesting proof of an identity attribute.
- The Proof: A cryptographic protocol that allows the prover to convince the verifier of the truth of their claim without revealing the secret information.
Core Properties of Zero-Knowledge Proofs:
- Completeness: If the statement is true and both the prover and verifier are honest, the verifier will be convinced.
- Soundness: If the statement is false, a dishonest prover cannot (with very high probability) convince an honest verifier that it is true.
- Zero-Knowledge: The verifier learns nothing beyond the fact that the statement is true. No actual data from the prover's identity is exposed.
To get a Zero Knowledge proof back from Google Wallet, you need to change the
request format to mso_mdoc_zk and add zk_system_type to your Request
...
"dcql_query": {
"credentials": [{
"id": "cred1",
"format": "mso_mdoc_zk",
"meta": {
"doctype_value": "org.iso.18013.5.1.mDL"
"zk_system_type": [
{
"system": "longfellow-libzk-v1",
"circuit_hash": "f88a39e561ec0be02bb3dfe38fb609ad154e98decbbe632887d850fc612fea6f", // This will differ if you need more than 1 attribute.
"num_attributes": 1, // number of attributes (in claims) this has can support
"version": 5,
"block_enc_hash": 4096,
"block_enc_sig": 2945,
}
{
"system": "longfellow-libzk-v1",
"circuit_hash": "137e5a75ce72735a37c8a72da1a8a0a5df8d13365c2ae3d2c2bd6a0e7197c7c6", // This will differ if you need more than 1 attribute.
"num_attributes": 1, // number of attributes (in claims) this has can support
"version": 6,
"block_enc_hash": 4096,
"block_enc_sig": 2945,
}
],
"verifier_message": "challenge"
},
"claims": [{
...
"client_metadata": {
"jwks": {
"keys": [ // sample request encryption key
{
...
You will get an encrypted zero knowledge proof back from the wallet. You can validate this proof against issuers IACA certs using Google's longfellow-zk library.
The verifier-service contains a deployment-ready, Docker-based server that lets you validate the response against certain issuer IACA certs.
You can modify the certs.pem to manage IACA issuer certs that you want to trust.
You can reach out to the support email for more details:
wallet-identity-rp-support@google.com
