This page explains the benefits of FedCM, who should consider implementing FedCM and how users interact with FedCM.
Federated Credential Management (FedCM) is a privacy-centric and user-friendly approach to federated identity services (such as Sign in with Identity Provider) that doesn't rely on third-party cookies or navigational redirects.
With FedCM, the user is introduced with a new way to authenticate on a website with a third-party identity provider.
What is identity federation
Identity federation delegates authentication or authorization of an individual (user or entity) to a trusted external identity provider (IdP). The IdP then allows the individual to sign in to a relying party website (RP). With identity federation, an RP relies on an IdP to provide the user an account without requiring a new username and password.
With federated identity solutions, the user doesn't have to create another set of credentials for every RP. This improves user experience, reduces the chances of phishing, and helps to acquire verified user information from trusted identity providers.
Traditional solutions and third party cookies
Traditional identity federation mechanisms rely on iframes, redirects or third-party cookies, causing privacy concerns. These solutions can be exploited for tracking users across the web, and browsers aren't able to distinguish between legitimate identity services and unwanted surveillance.
With the privacy concern in mind, major browsers are restricting third-party cookies. This may affect some functionalities. Through community effort and our research, we learned there are a few identity federation related integrations that are affected by third-party cookie restrictions.
Identity federation with FedCM
FedCM aims to enable these crucial authentication flows even for the users who choose to browse with third-party cookies restricted.
FedCM is protocol-agnostic: it can be implemented as a standalone solution or as an additional layer that different protocols can take advantage of. For example, a functional OAuth server can benefit from the FedCM's browser-mediated one-tap login experience and intuitive UI by implementing FedCM endpoints and then exchanging the authorization code returned in FedCM's response for an OAuth access token.
Why do we need FedCM?
Compared to traditional solutions, it offers multiple benefits for the web ecosystem, designed with the user, the RPs and IdPs developers in mind.
Support for identity solutions without third-party cookies
FedCM can help reduce reliance on third-party cookies, which are often used to track users across the web. The API offers a personalized sign in experience even for those users who choose to browse with third-party cookies restricted.
FedCM is also integrated with other Privacy Sandbox APIs. For example, the Storage Access API uses FedCM authentication as a trust signal. This integration is useful for the websites that rely on both FedCM for authentication and the SAA to enable cross-origin iframes to access necessary storage.
Improved user experience
FedCM introduces a browser-mediated UI dialog for a simplified one-tap login process. The API also addresses the issue of cluttered login pages, sometimes called the NASCAR problem.
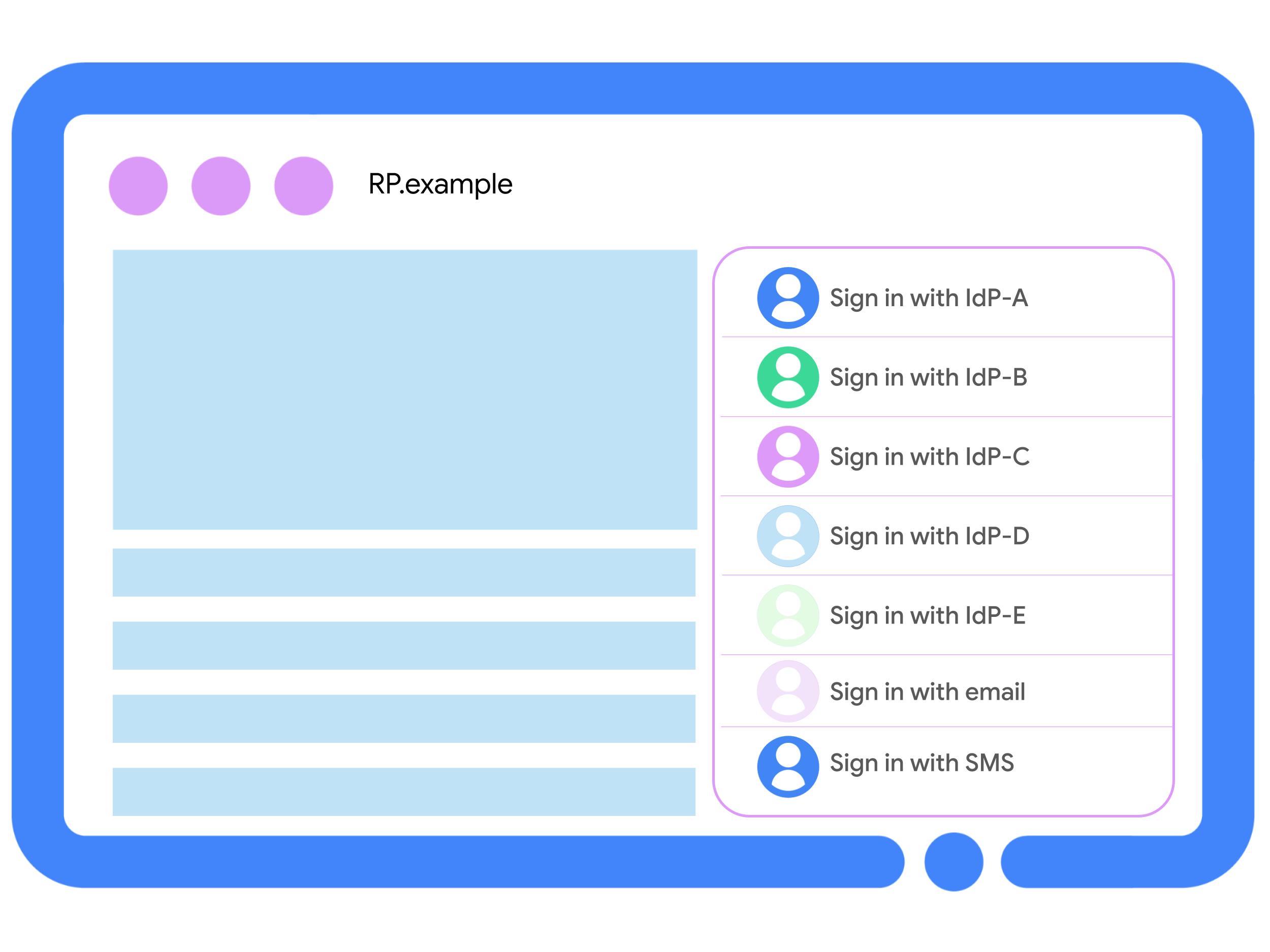
Instead of an overwhelming number of social login buttons, FedCM provides a simpler user-friendly interface.
Security
The Federated Identity approach enables users to use trusted accounts managed by IdPs. With this approach, users don't have to add credentials to every site. This reduces the surface for phishing attacks. Additionally, instead of implementing their own robust security measures, RPs can rely on the expertise of IdPs who specialize in secure identity management.
FedCM aims to make the federated identity flow even more convenient for users, encouraging them to prefer it over less secure identity flows.
Personalized experience for more users
FedCM reduces UX friction during the account sign up flow. Google Identity Service's case studies show that users prefer creating accounts with FedCM's One Tap flow over multi-step sign-in options.
With FedCM, more IdPs can offer their users a one-tap sign-in experience. With more IdPs offering a one-tap identity flow, users can choose from a wider selection of IdPs on RPs. FedCM provides an improvedIdP selection mechanism by presenting the users with most relevant accounts.
With higher signup rates, RPs can offer personalized experience to more users.
Support for diverse Identity Providers
FedCM's simplified UI aims to present users with a personalized list of the
relevant IdPs.
With FedCM's IdP selection mechanism, RP's choice of IdPs is no longer
restricted by how large the IdP's user base is. For example, a portion of users
may have an account only with small-idp.example, and not with
bigger-idp.example.
With the Multi-IdP feature,
rp.example can support both small-idp.example and bigger-idp.example
without cluttering the UI. This benefits all of the parties:
- Users can choose their preferred IdP, no matter how big or small.
- RPs reach more users through diverse IdP support
- IdPs with a smaller user base are available on more RPs.
Who should use FedCM?
We expect FedCM to be useful to you only if these conditions apply:
- You aim to support federated identity flows even for users who opt for browsing without third-party cookies.
- You're an identity provider (IdP) with third-party RPs. If your RPs are meaningfully related sites, you may be better served by Related Website Sets.
- You have your own identity solution and multiple domains relying on it.
You're an IdP
FedCM requires support from an identity provider. A relying party cannot use FedCM independently. If you are an RP, you can ask your IdP to provide instructions.
Multiple RPs
If your RPs are third-party, or you have more than four RPs using your identity solution, FedCM is the recommended API for federated identity.
If you're an identity provider with up to five RPs, and the RPs have a first-party relationship to IdP, consider using Related Website Sets (RWS). RWS allows for limited third-party cookie access across sets of meaningfully related sites, even when third-party cookies are otherwise restricted.
You aim to support cookieless identity federation flow
FedCM supports essential federated identity flows even for users who opt for browsing without third-party cookies. With FedCM, users can still sign-up, sign-in and sign-out with their federated accounts on RPs.
Additionally, FedCM serves as a trust signal for Storage Access API, eliminating friction for IdP-initiated storage access requests.
Test whether your identity federation will continue to work for users who choose to browse without third-party cookies by blocking third-party cookies on Chrome. Make sure to test these known features that third-party cookie restrictions are expected to affect.
User interaction with FedCM
FedCM is designed to be authentication protocol-agnostic and offers the user a new flow to authenticate to an RP with a third-party IdP. Try FedCM with our demo.
Sign in to a relying party
FedCM has two UI modes: Passive and Active.
Passive mode. Passive mode doesn't require user interaction for the FedCM
prompt to appear. When the user lands on the relying party (RP) website, a FedCM
sign-in dialog may appear when navigator.credentials.get() is called if the
following conditions are met:
- The user is signed in to the IdP.
- The FedCM cooldown setting is not set in the user's browser.
- The user did not disable FedCM in their browser settings. Learn more about how users can opt out of FedCM.
Active mode. In active mode, a transient user activation (such as Sign in with… button click) is required to trigger a FedCM prompt.
The user can complete sign in by tapping Continue as <user>. If successful, the browser stores the fact that the user has created a federated account on the RP with the IdP.
If the user doesn't have an account on the RP with the IdP, a sign-up dialog appears with additional disclosure text such as the RP's terms of service and privacy policy.
Compliance with ePrivacy laws
Using FedCM, either as an IdP or an RP, involves the storage of information on a user's terminal equipment or access to information already stored in it, and is therefore an activity subject to ePrivacy laws in the European Economic Area (EEA) and the UK generally requiring user consent. It is your responsibility to determine whether your use of FedCM is strictly necessary to provide an online service explicitly requested by the user, and therefore exempt from the consent requirement. For more information, we encourage you to read our Privacy Sandbox Privacy-related Compliance FAQs.
Vision
We are actively developing new features to address current limitations and offer better user experience.
- We are exploring quieter UX formulations to ensure a smooth,intuitive and less intrusive authentication process for the users.
- We are dedicated to improving user privacy. We plan to transition to the delegation-oriented NextGen FedCM model that mitigates the IdP Tracking Problem. With NextGen, users can login on RPs without the IdP following the user.
- FedCM aims to present users with a wider selection of IdPs, based on the RP's choice. To achieve this, we're working on the Multi-IdP and the IdP Registration APIs.
- We are actively working to integrate FedCM with other authentication methods like Passkeys with additional means such as Autofill to introduce a unified authentication experience.
See our roadmap for more detail.
