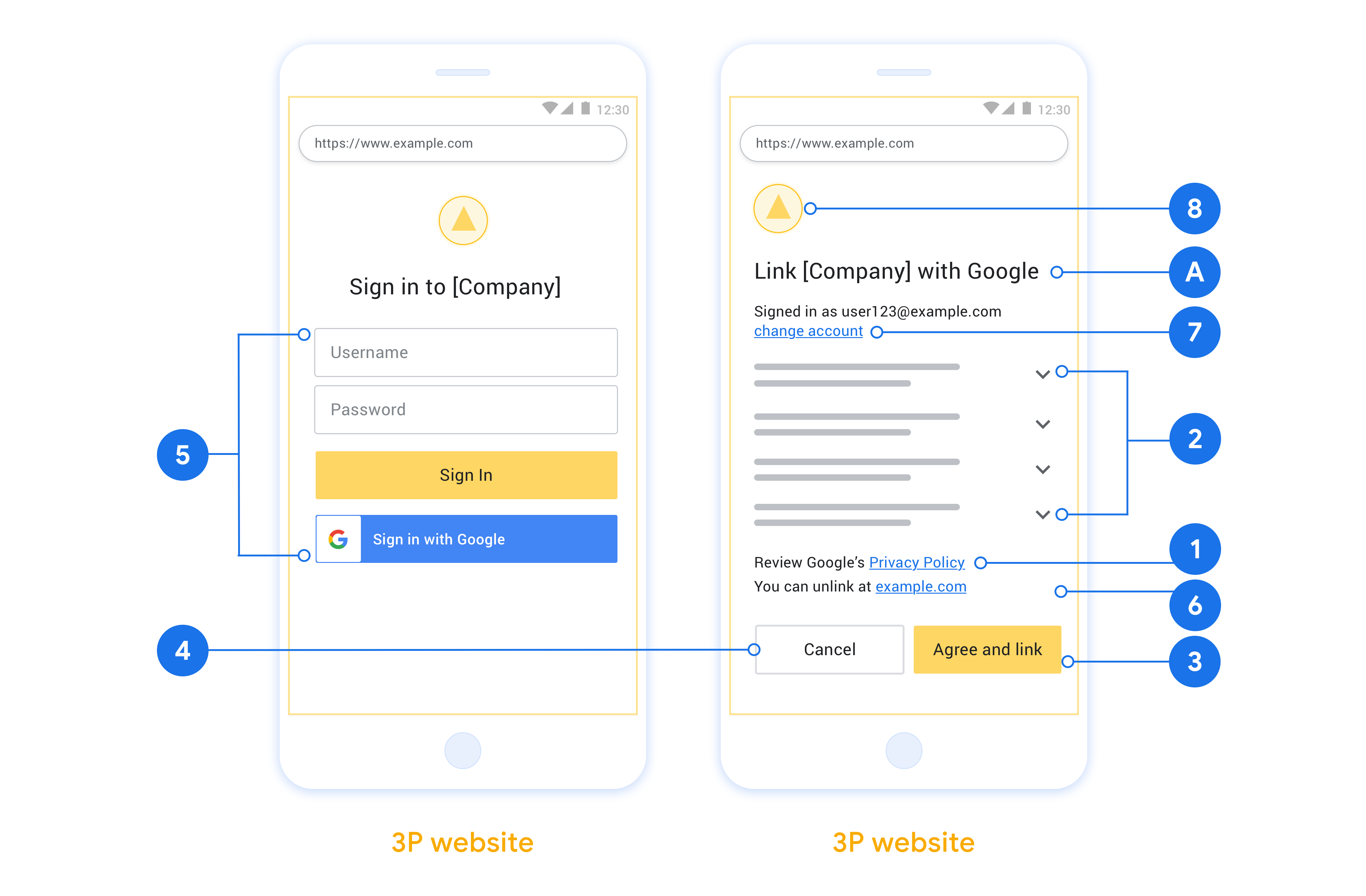
帳戶連結會使用業界標準的 OAuth 2.0 隱含和授權碼流程。您的服務必須支援符合 OAuth 2.0 標準的授權和權杖交換端點。
In the implicit flow, Google opens your authorization endpoint in the user's browser. After successful sign in, you return a long-lived access token to Google. This access token is now included in every request sent from Google.
In the authorization code flow, you need two endpoints:
The authorization endpoint, which presents the sign-in UI to your users that aren't already signed in. The authorization endpoint also creates a short-lived authorization code to record users' consent to the requested access.
The token exchange endpoint, which is responsible for two types of exchanges:
- Exchanges an authorization code for a long-lived refresh token and a short-lived access token. This exchange happens when the user goes through the account linking flow.
- Exchanges a long-lived refresh token for a short-lived access token. This exchange happens when Google needs a new access token because the one it had expired.
Choose an OAuth 2.0 flow
Although the implicit flow is simpler to implement, Google recommends that access tokens issued by the implicit flow never expire. This is because the user is forced to link their account again after a token expires with the implicit flow. If you need token expiration for security reasons, we strongly recommend that you use the authorization code flow instead.
Design guidelines
This section describes the design requirements and recommendations for the user screen that you host for OAuth linking flows. After it's called by Google's app, your platform displays a sign in to Google page and account linking consent screen to the user. The user is directed back to Google's app after giving their consent to link accounts.
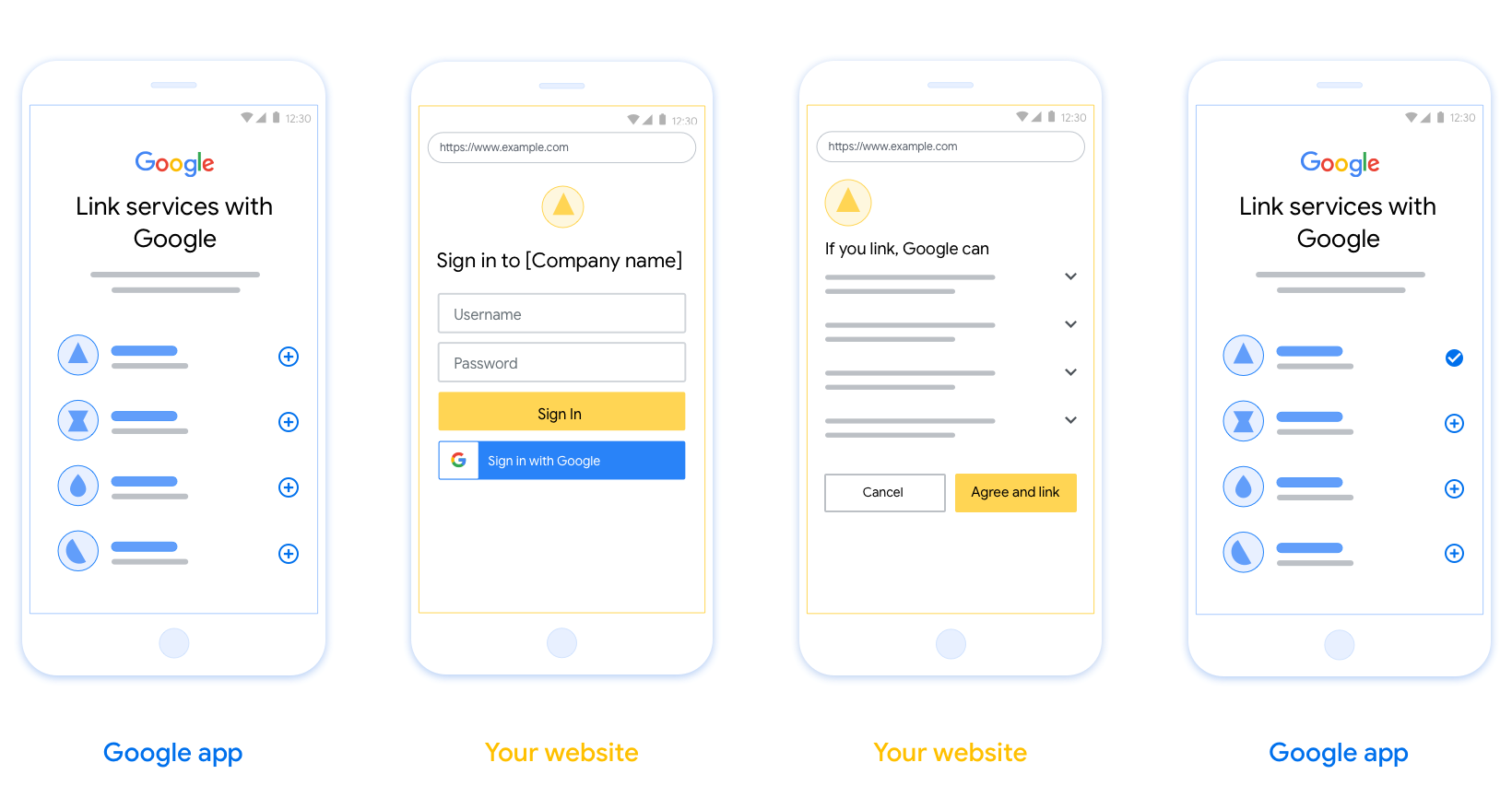
Requirements
- You must communicate that the user’s account will be linked to Google, not a specific Google product like Google Home or Google Assistant.
Recommendations
We recommend that you do the following:
Display Google's Privacy Policy. Include a link to Google’s Privacy Policy on the consent screen.
Data to be shared. Use clear and concise language to tell the user what data of theirs Google requires and why.
Clear call-to-action. State a clear call-to-action on your consent screen, such as “Agree and link.” This is because users need to understand what data they're required to share with Google to link their accounts.
Ability to cancel. Provide a way for users to go back or cancel, if they choose not to link.
Clear sign-in process. Ensure that users have clear method for signing in to their Google account, such as fields for their username and password or Sign in with Google.
Ability to unlink. Offer a mechanism for users to unlink, such as a URL to their account settings on your platform. Alternatively, you can include a link to Google Account where users can manage their linked account.
Ability to change user account. Suggest a method for users to switch their account(s). This is especially beneficial if users tend to have multiple accounts.
- If a user must close the consent screen to switch accounts, send a recoverable error to Google so the user can sign in to the desired account with OAuth linking and the implicit flow.
Include your logo. Display your company logo on the consent screen. Use your style guidelines to place your logo. If you wish to also display Google's logo, see Logos and trademarks.
建立專案
如要建立專案以使用帳戶連結,請按照下列步驟操作:
- 按一下 [Create Project]。
- 輸入名稱或接受系統產生的建議。
- 確認或編輯其餘欄位。
- 點選「建立」。
如要查看專案 ID,請按照下列步驟操作:
- 在到達網頁的表格中找出專案。專案 ID 會顯示在「ID」欄中。
設定 OAuth 同意畫面
Google 帳戶連結程序會顯示同意畫面,告知使用者要求存取資料的應用程式、要求存取的資料類型,以及適用條款。您必須先設定 OAuth 同意畫面,才能產生 Google API 用戶端 ID。
- 開啟 Google API 控制台的「OAuth 同意畫面」頁面。
- 如果出現提示,請選取您剛建立的專案。
在「OAuth 同意畫面」頁面中填寫表單,然後按一下「儲存」按鈕。
應用程式名稱:要求同意的應用程式名稱。名稱應如實反映應用程式,且與使用者在其他地方看到的應用程式名稱一致。應用程式名稱會顯示在帳戶連結同意畫面上。
應用程式標誌:同意畫面上的圖片,可協助使用者識別您的應用程式。標誌會顯示在帳戶連結同意畫面和帳戶設定頁面。
支援電子郵件地址:方便使用者與您聯絡,洽詢同意聲明相關事宜。
Google API 的範圍:範圍可讓應用程式存取使用者的私人 Google 資料。如果是 Google 帳戶連結用途,預設範圍 (電子郵件、個人資料、openid) 就已足夠,不需要新增任何敏感範圍。一般而言,最佳做法是在需要存取權時,逐步要求範圍,而非預先要求。瞭解詳情。
授權網域:為保障您與使用者的安全,Google 只允許應用程式透過 OAuth 驗證,使用授權網域。應用程式的連結必須託管於授權網域。瞭解詳情。
應用程式首頁連結:應用程式的首頁。必須託管在授權網域。
應用程式隱私權政策連結:顯示在 Google 帳戶連結同意畫面上。必須託管在授權網域。
應用程式服務條款連結 (選填):必須代管於授權網域。
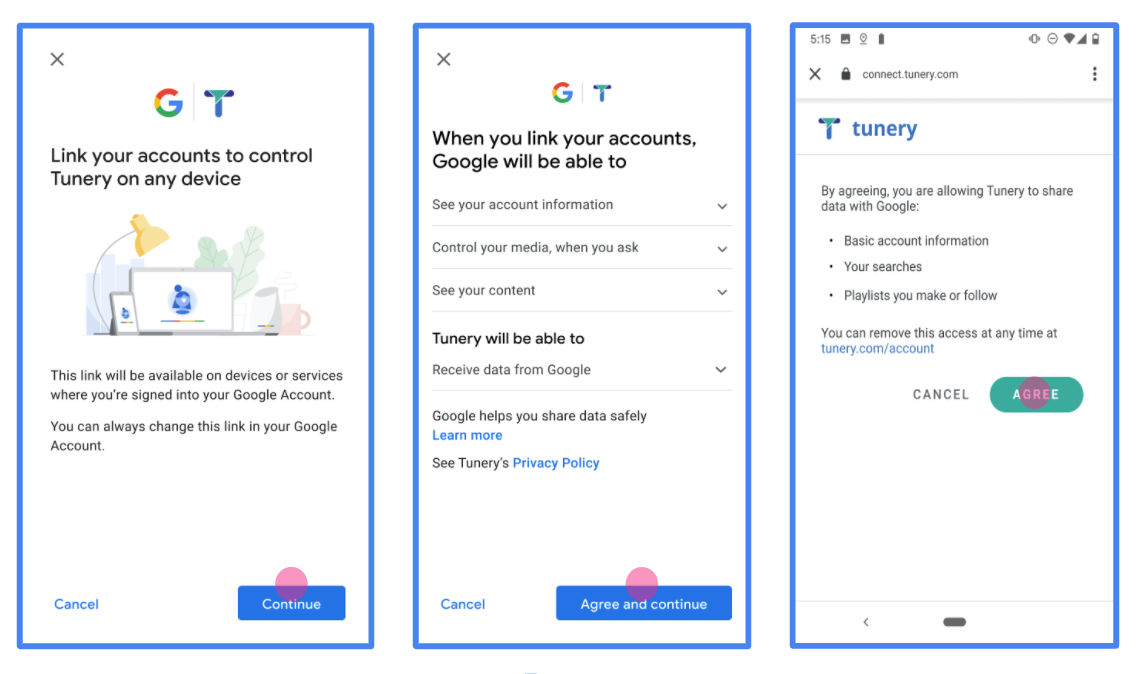
圖 1. 虛構應用程式 Tunery 的 Google 帳戶連結同意畫面
查看「驗證狀態」,如果應用程式需要驗證,請點按「送交驗證」按鈕,將應用程式送交驗證。詳情請參閱 OAuth 驗證規定。
實作 OAuth 伺服器
如要支援 OAuth 2.0 隱含流程,服務會進行授權 並可透過 HTTPS 存取端點這個端點會負責驗證 徵得使用者同意,才能存取資料。授權端點 為使用者提供未登入並記錄登入的登入使用者介面 同意授予請求的存取權。
當 Google 應用程式需要呼叫服務的其中一個已授權 API 時, Google 會使用這個端點,向使用者取得呼叫這些 API 的權限 管理。
由 Google 發起的一般 OAuth 2.0 隱含流程工作階段,是 下列流程:
- Google 會在使用者的瀏覽器中開啟授權端點。 使用者登入 (如果尚未登入),並將權限授予 Google 透過您的 API 存取他們的資料 (如果尚未授予權限)。
- 您的服務會建立存取權杖,並傳回給 Google。若要這麼做,請將使用者的瀏覽器重新導向回 Google,並授予存取權 附加至請求的權杖
- Google 會呼叫服務的 API,並將存取權杖附加至 每個要求您的服務會確認存取權杖是否已授予 Google 授權存取 API,然後完成 API 呼叫。
處理授權要求
Google 應用程式需要透過 OAuth 2.0 進行帳戶連結時 隱含流程時,Google 會將使用者傳送至您的授權端點, ,其中包含下列參數:
| 授權端點參數 | |
|---|---|
client_id |
您指派給 Google 的用戶端 ID。 |
redirect_uri |
您傳送回應到這項要求的網址。 |
state |
傳回給 Google 的記帳金額,值維持不變 重新導向 URI |
response_type |
要在回應中傳回的值類型。以 OAuth 2.0 隱含
回應類型則一律為 token。 |
user_locale |
中的 Google 帳戶語言設定 RFC5646 將內容翻譯成使用者慣用的語言。 |
舉例來說,如果您的授權端點位於
https://myservice.example.com/auth,要求可能如下所示:
GET https://myservice.example.com/auth?client_id=GOOGLE_CLIENT_ID&redirect_uri=REDIRECT_URI&state=STATE_STRING&response_type=token&user_locale=LOCALE
如要讓授權端點處理登入要求,請按照下列步驟操作: 步驟:
確認
client_id和redirect_uri的值如下: 防止授予非預期或設定錯誤的用戶端應用程式存取權:- 確認
client_id與您用戶端 ID 相符 而是指派給 Google - 確認
redirect_uri指定的網址 參數的格式如下:https://oauth-redirect.googleusercontent.com/r/YOUR_PROJECT_ID https://oauth-redirect-sandbox.googleusercontent.com/r/YOUR_PROJECT_ID
- 確認
檢查使用者是否已登入您的服務。如果使用者未簽署 的登入或申請流程。
產生供 Google 存取 API 的存取權杖。 存取權杖可以是任何字串值,但必須明確代表 以及該權杖適用的用戶端,且不可猜測。
傳送 HTTP 回應,將使用者的瀏覽器重新導向至網址 由
redirect_uri參數指定。包含所有 網址片段中的下列參數:access_token:您剛剛產生的存取權杖token_type:字串bearerstate:原始資料中未經修改的狀態值 要求
以下是最終網址的範例:
https://oauth-redirect.googleusercontent.com/r/YOUR_PROJECT_ID#access_token=ACCESS_TOKEN&token_type=bearer&state=STATE_STRING
Google 的 OAuth 2.0 重新導向處理常式收到存取權杖並確認
state 值未變更。Google 取得
服務存取權杖,Google 會將該權杖附加到後續的呼叫
以便將 API 新增至 Service API
Handle userinfo requests
The userinfo endpoint is an OAuth 2.0 protected resource that return claims about the linked user. Implementing and hosting the userinfo endpoint is optional, except for the following use cases:
- Linked Account Sign-In with Google One Tap.
- Frictionless subscription on AndroidTV.
After the access token has been successfully retrieved from your token endpoint, Google sends a request to your userinfo endpoint to retrieve basic profile information about the linked user.
| userinfo endpoint request headers | |
|---|---|
Authorization header |
The access token of type Bearer. |
For example, if your userinfo endpoint is available at
https://myservice.example.com/userinfo, a request might look like the following:
GET /userinfo HTTP/1.1 Host: myservice.example.com Authorization: Bearer ACCESS_TOKEN
For your userinfo endpoint to handle requests, do the following steps:
- Extract access token from the Authorization header and return information for the user associated with the access token.
- If the access token is invalid, return an HTTP 401 Unauthorized error with using the
WWW-AuthenticateResponse Header. Below is an example of a userinfo error response:HTTP/1.1 401 Unauthorized WWW-Authenticate: error="invalid_token", error_description="The Access Token expired"
If the access token is valid, return and HTTP 200 response with the following JSON object in the body of the HTTPS response:
{ "sub": "USER_UUID", "email": "EMAIL_ADDRESS", "given_name": "FIRST_NAME", "family_name": "LAST_NAME", "name": "FULL_NAME", "picture": "PROFILE_PICTURE", }userinfo endpoint response subA unique ID that identifies the user in your system. emailEmail address of the user. given_nameOptional: First name of the user. family_nameOptional: Last name of the user. nameOptional: Full name of the user. pictureOptional: Profile picture of the user.
驗證實作
您可以使用 OAuth 2.0 Playground 工具驗證實作結果。
請在工具中按照下列步驟操作:
- 點選「Configuration」圖示 ,開啟 OAuth 2.0 設定視窗。
- 在「OAuth 流程」欄位中,選取「用戶端」。
- 在「OAuth 端點」欄位中,選取「自訂」。
- 在對應的欄位中指定 OAuth 2.0 端點,以及您指派給 Google 的用戶端 ID。
- 在「步驟 1」部分中,請勿選取任何 Google 範圍。請改為將這個欄位留空,或輸入有效的伺服器範圍 (如果您不使用 OAuth 範圍,則輸入任意字串)。完成後,按一下「授權 API」。
- 在「步驟 2」和「步驟 3」部分,請完成 OAuth 2.0 流程,並確認每個步驟都能正常運作。
您可以使用 Google 帳戶連結示範工具驗證實作成果。
在工具中執行下列步驟:
- 按一下「使用 Google 帳戶登入」按鈕。
- 選擇要連結的帳戶。
- 輸入服務 ID。
- 您可以選擇輸入一或多個要申請存取權的範圍。
- 按一下「開始試用」。
- 系統顯示提示時,請確認您可以同意或拒絕連結要求。
- 確認系統是否會將你重新導向至平台。
